Wie können wir helfen?
Decrypting REDDCRYPT Emails with standard OpenPGP tools
One of our goals for REDDCRYPT is to enable everyone to easily encrypt emails while retaining security. Because of this we use OpenPGP as our underlying encryption method and automated the complete certificate creation and the exchange of public keys.
Even though we removed the complexity of the key management for the end user, it is still possible to decrypt emails with standard OpenPGP tools if necessary.
We will explain how this works in the following.
Requirements
In order to manually decrypt REDDCRYPT emails you may use any tool able to decrypt OpenPGP files. In this manual we shall look at GnuPG command line tools as an example: https://gnupg.org/ftp/gcrypt/binary/
In this example we work with the application for Windows. Please install the current version of: gnupg-w32-<version>.exe
Please note: The following commands should normally also work under Linux and Mac OSX if the necessary GnuPG tools are installed.
Importing the REDDCRYPT private key to the OpenPGP key ring
In order to decrypt a REDDCRYPT email you will always need your own private key. You can export your private key in the REDDCRYPT web app and import it to your OpenPGP key ring.
After saving your private key you can import the key to your OpenPGP key ring with the following command:
gpg --import privatekey.ascYou may be asked for your password upon importing or when using the key depending on the PGP tool.
Decrypting a REDDCRYPT email via command line
To decrypt a REDDCRYPT email, simply save the encrypted attachment from the REDDCRYPT transport mail.
Now you can decrypt the file with the following command:
gpg --decrypt --output decrypted.eml reddcrypt.securemail- With the parameter –decrypt the function to decrypt is selected.
- With the parameter –output you can define the file name of the decrypted mail.
The OpenPGP tool will ask you for the password for your private key. Here you have to use the password of your REDDCRYPT account.
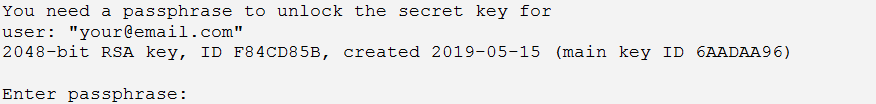
Upon successful password entry, the mail will be decrypted.

This warning is due to the fact that a sender’s public key is needed for checking the signature. However, this public key cannot automatically be accessed by PGP tools.
The public key will automatically be accessed and the signature checked when decrypting emails with one of the REDDCRYPT applications.
Checking the signature of a REDDCRYPT email via command line
To check the signature of a REDDCRYPT email the sender’s public key can be retrieved manually for test purposes.
Important: The retrieval of public keys via the standard protocol (HKP) should only be used for test purposes. In contrast to the standard PGP key servers REDDCRYPT does not allow unlimited access to public keys.
- Retrieving email addresses is not possible
- Access is limited to one query per minute
To get the matching public key for checking of the signature, the key ID is needed. The key ID is shown after the decryption of an email.
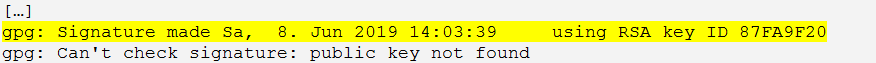
In the example shown above the ID of the key that was used for signing is 87FA9F20.
To retrieve the public key with this ID from the REDDCRYPT key server, the following command can be used:
gpg --keyserver hkps://keys.reddcrypt.com --recv-keys 87FA9F20The public key will then be imported to your OpenPGP key ring automatically.
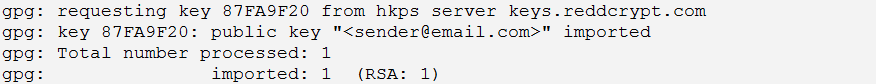
Now the email can be decrypted again and the signature will be checked as well.

